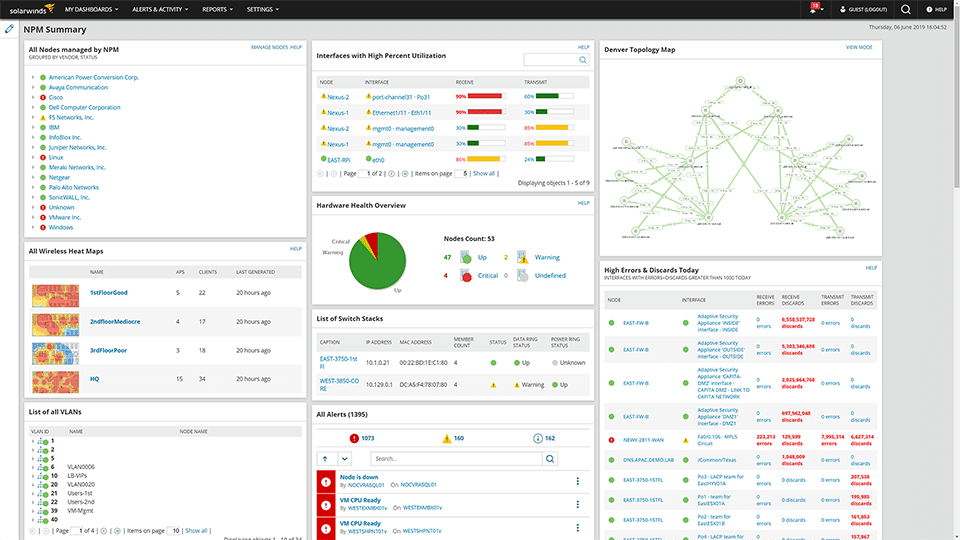
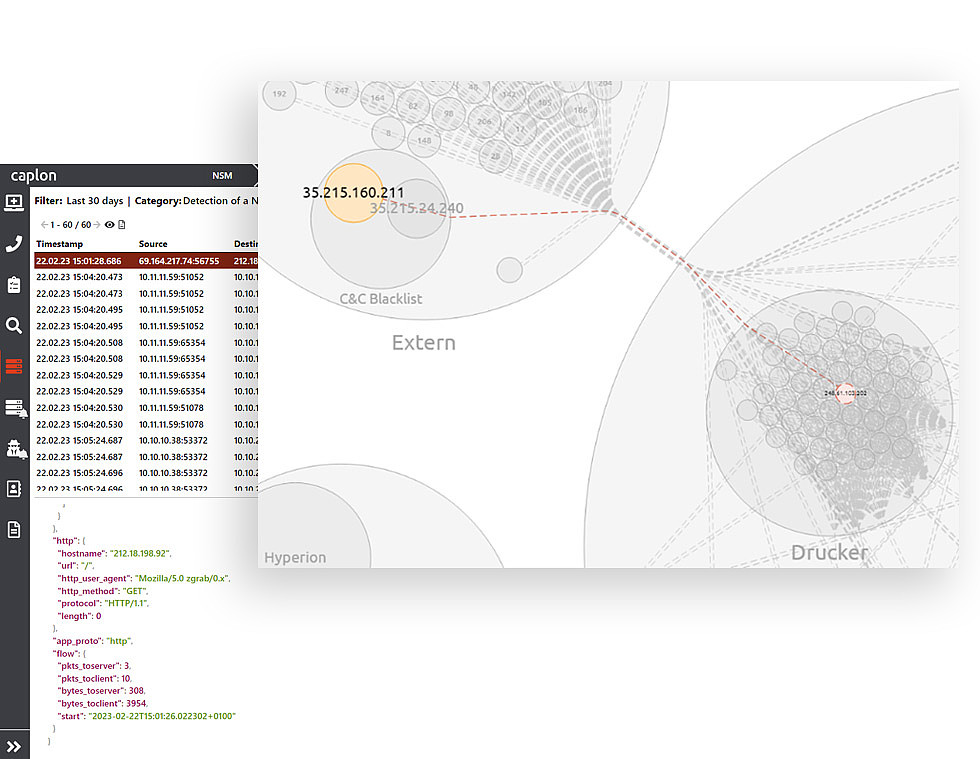
Checklist for Network Security Monitoring (NSM) for On-premise, Data Centers and Cloud set-ups – Detecting anomalous network patterns

Applied Network Security Monitoring: Collection, Detection, and Analysis : Sanders, Chris, Smith, Jason: Amazon.de: Bücher

Applied Network Security Monitoring: Collection, Detection, and Analysis : Sanders, Chris, Smith, Jason: Amazon.de: Bücher