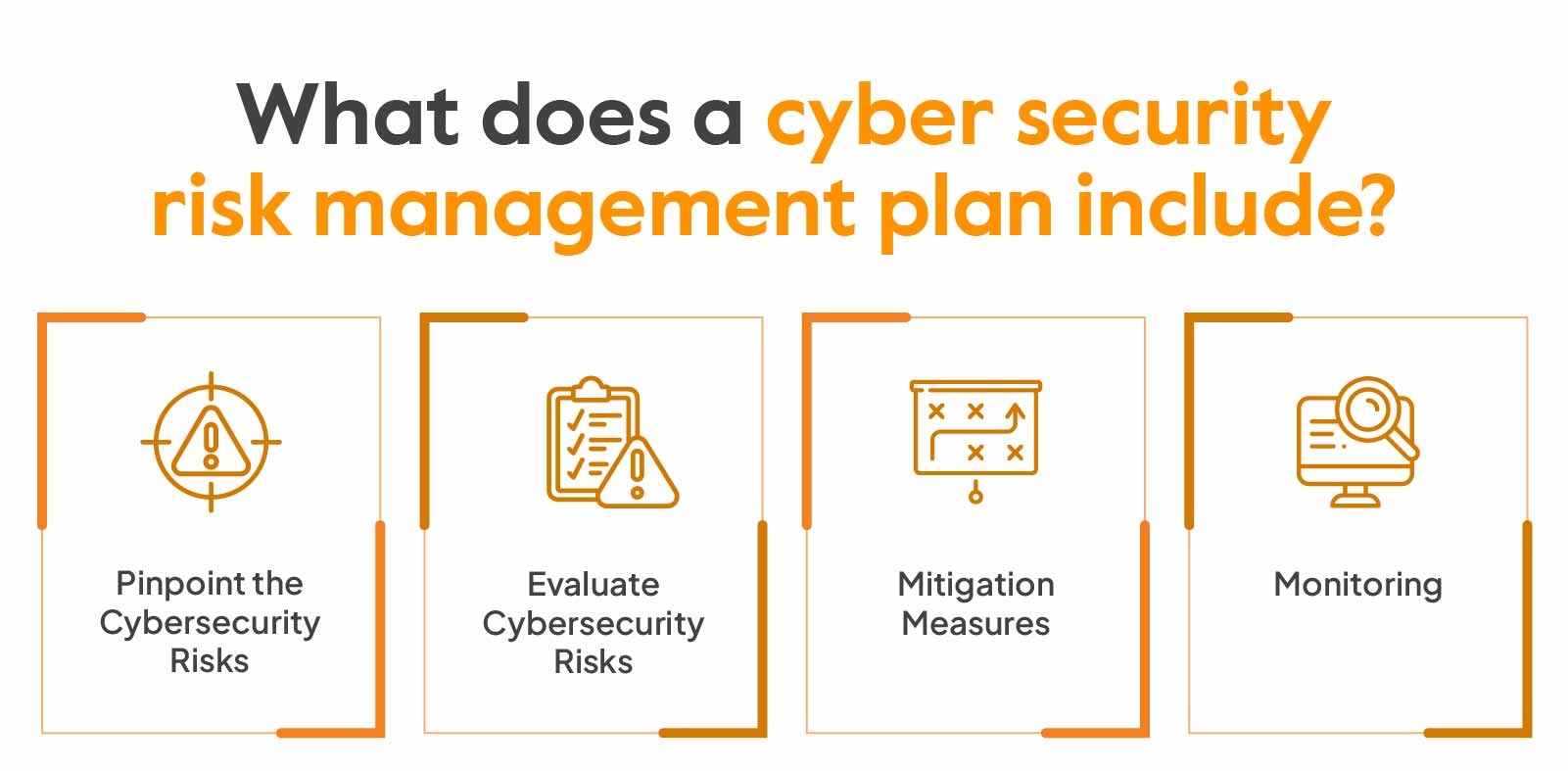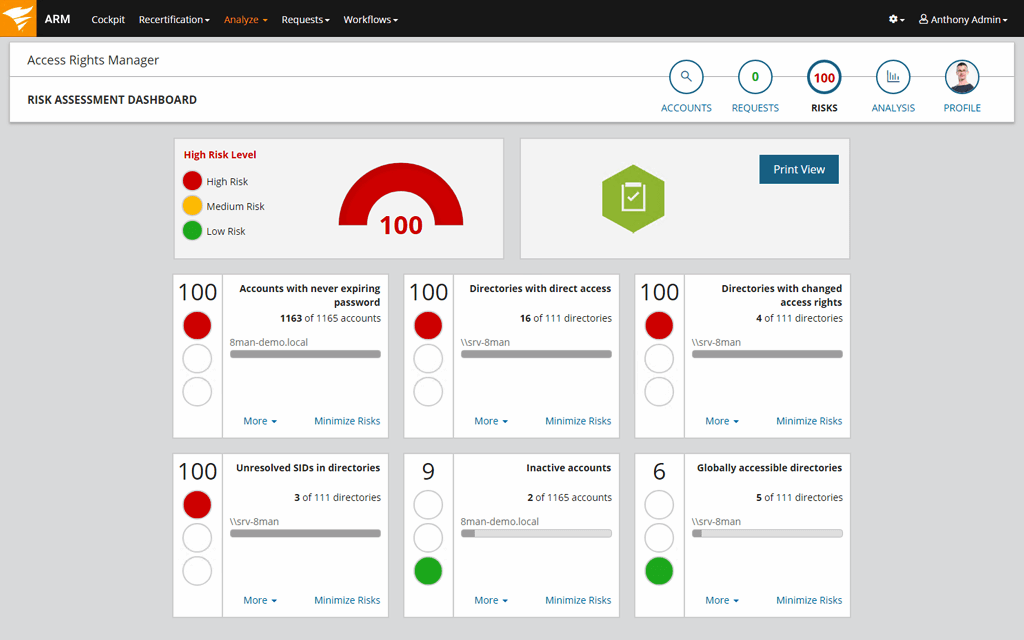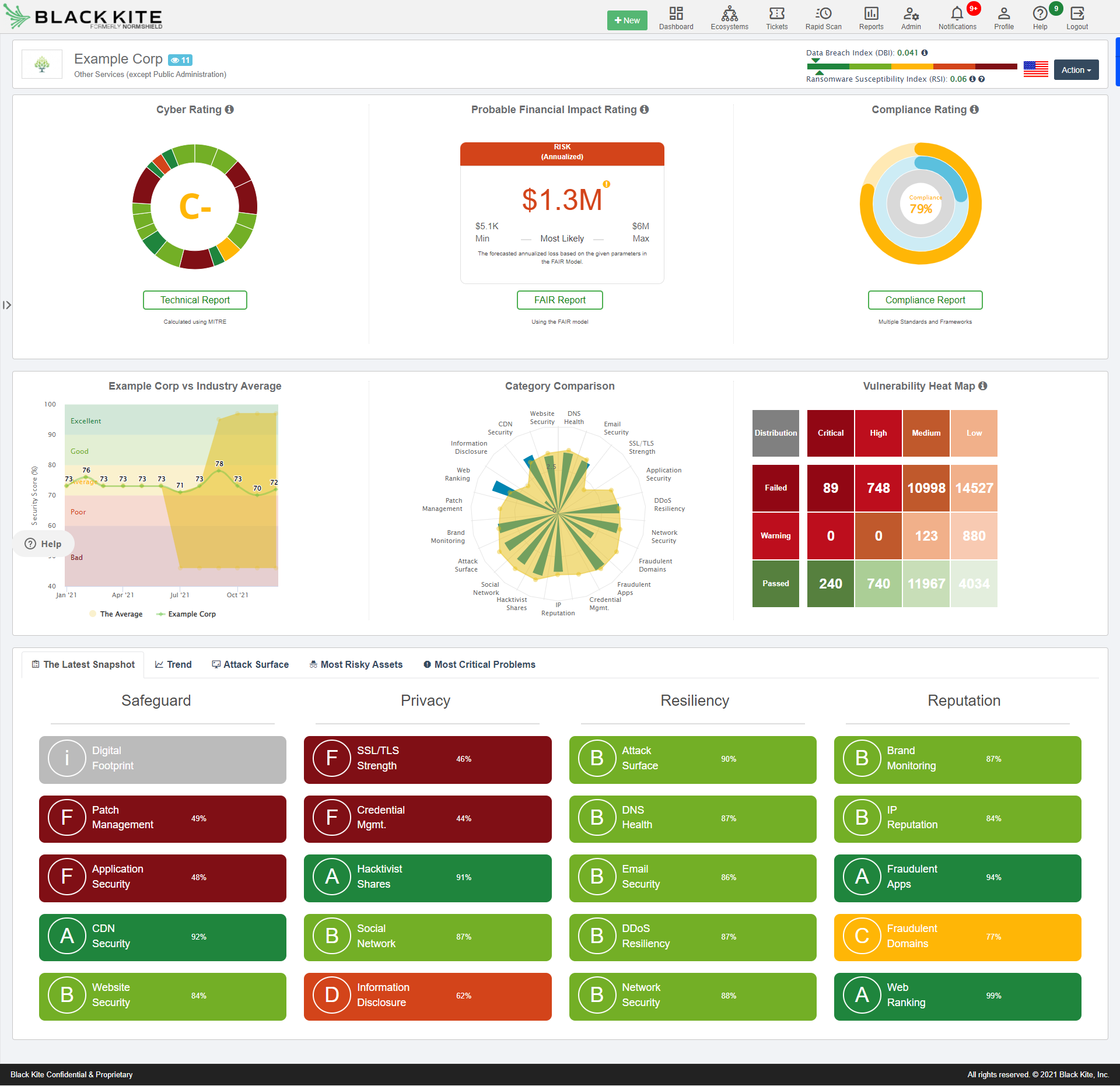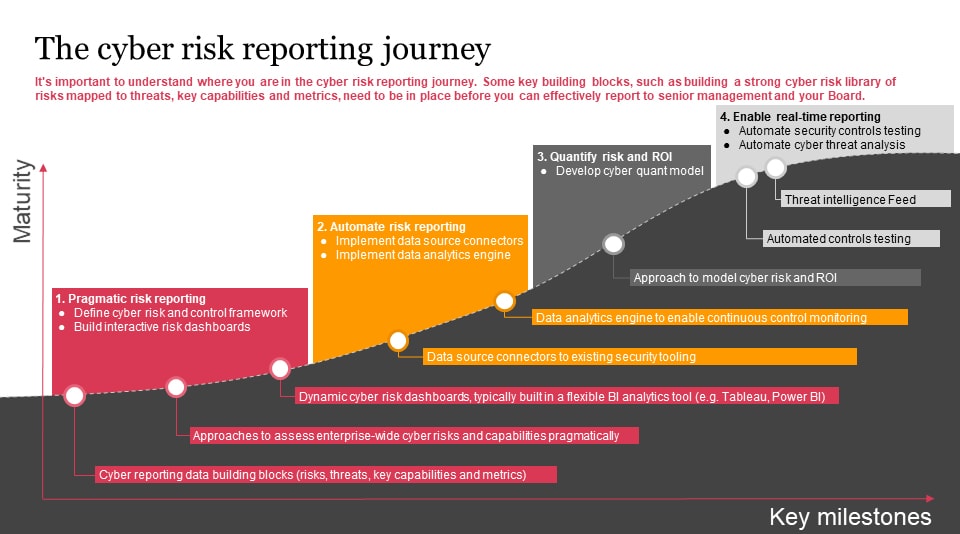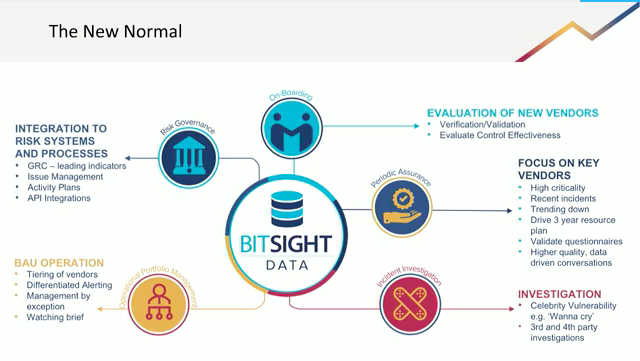
On-Demand: Cybersecurity Ratings Part 1: Continuous Cyber Risk Monitoring - Adapting to the New Normal | Bitsight
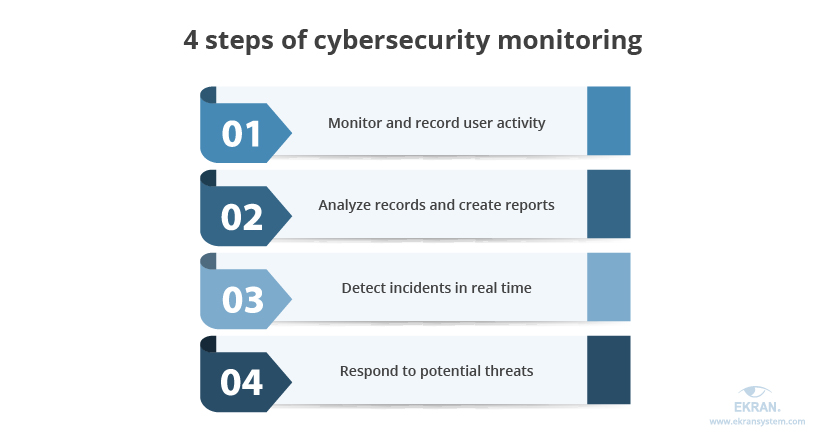
4 Steps to Ensuring Efficient Cybersecurity Monitoring in US Educational Institutions | Ekran System

Avetta Launches Cyber Risk Solution to Give Companies 24/7 Visibility of Cybersecurity Risks in Their Supply Chain | Avetta | AU